Wpa Cracking Gpu Benchmark

Today We will learn about Cracking the Hashes using CPU and GPU. CPU: Central Processing Unit GPU: Graphical Processing Unit We will cover: • What is a Hash? • What is the need of a Hash? Drift N Burn 365 Download Games. Risiko 2 Pc Spiel Kostenlos. • Why Hash over Encryption or Encoding? • Hardware configuration • Tools required • Hash cracking [CPU] • Hash cracking [GPU] • Hash cracking using Search engine • Why such a difference?
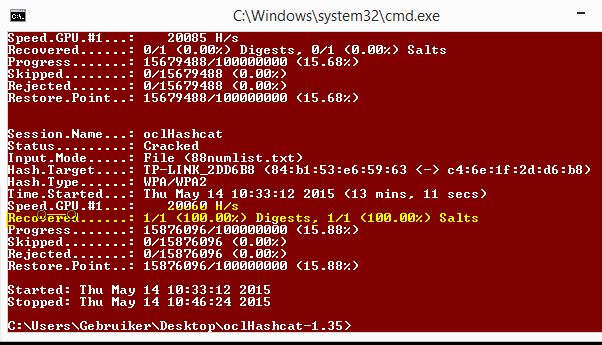
Wi-Fi Security: Cracking WPA With CPUs, GPUs. The Pyrit benchmark command is commonly used to highlight GPU performance. WPA Cracking: It Starts With.
What is a Hash? A Cryptographic function that converts a data or file of arbitrary length or size to a fixed length, which is considered practically impossible to invert.
See What is the need of a Hash? A major use of Hash is in the security field. To provide security or privacy to the user who is using any service of a company.
For example: You are using Gmail, Facebook, Twitter, eBay, Amazon or Online payment portals like Paypal. Where you use the service by providing your credentials(username/password) There are basically 2 reasons: • Making it difficult for hackers to recover/retrieve Password, Online service(Gmail,eBay etc) or even Wi-Fi. • Checking for the file verification. See SHA1 Even If company’s security is breached (Hacked), then also the user’s credentials are safe(only if you use strong password) Why Hash over Encryption and Encoding? Imagine a scenario, which perhaps happen to almost every Big banner, take it Google, Facebook, Yahoo! Download Free Rapidshare Carbon Copy Cloner Serial more. A website is compromised and User’s data(credentials) is compromised. What is the thing that will make you worry when you come to know that, if you are a registered user on that site?
Your Password (might be master password, for all your accounts). Now, It is in service provider’s hand to provide security to their consumers. Hence, Hashing is the solution. Well, you might be familiar with these terms: • Encoding/Decoding • Encrypt/Decrypt • and now, Hashing Not going into the details, I will tell you a basic and most important feature of Hash which makes Hash much different and important over Encoding and Decoding. And that is: Encoded text/file can be Decoded, Encrypted text/file can be Decrypted, But hashed text/file can never be De-hashed. Yes, Hash unlike Encryption/Encoding, is a One way process i.e when a text/file go through the Cryptographic hash function, it is converted into a fixed character length.